Cheatsheet
AV/EDR Bypass
TOOL---Invoke-Obfuscation#tool-info
Technique Info
Link to originalHow to Use Invoke-Obfuscation to Obfuscate PowerShell Scripts
Import-Module ./Invoke-Obfuscation.psd1 Invoke-Obfuscation # Then follow prompts: SET SCRIPTPATH C:\path\to\Invoke-Mimikatz.ps1 OKEN ALL 1 # Select obfuscation level 1 OUT C:\path\to\obfuscated-Invoke-Mimikatz.ps1
Commands
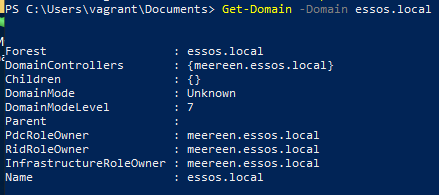
Get information on Domain
Command
Get-Domain # current domain Get-Domain -Domain essos.local # different domainExample
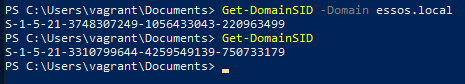
Get Domain SID
Command
Get-DomainSID # current domain Get-DomainSID -Domain essos.local # different domainExample
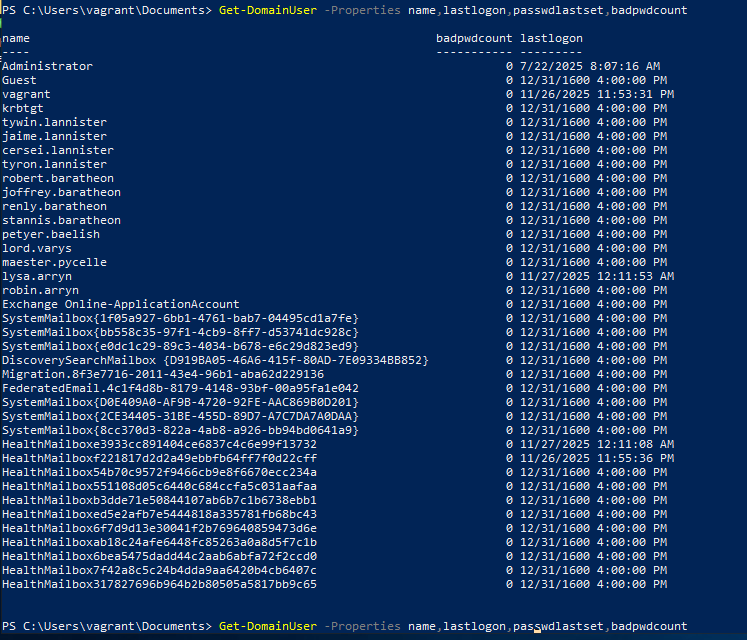
Get Domain Users
Command
# current domain Get-DomainUser -Properties name,lastlogon,passwdlastset,badpwdcount # different domain Get-DomainUser -Domain essos.local -Properties name,lastlogon,passwdlastset,badpwdcount ```Example
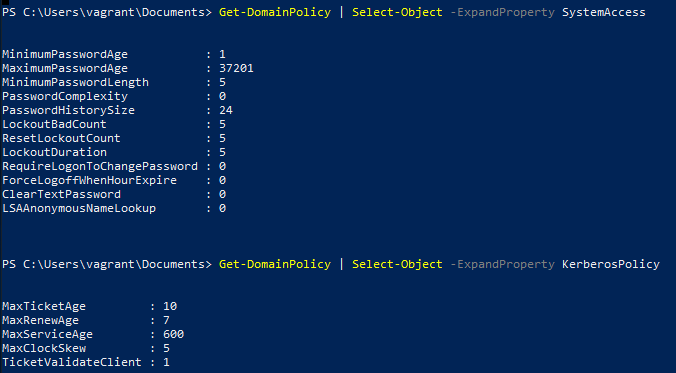
Get Domain Policy Information
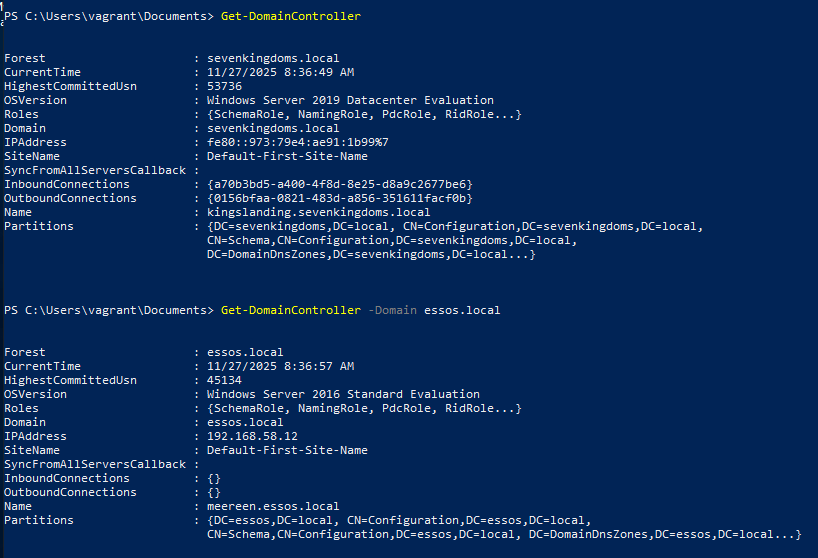
Get Domain Controller
Command
Get-DomainController # current domain Get-DomainController -Domain essos.local # different domainExample
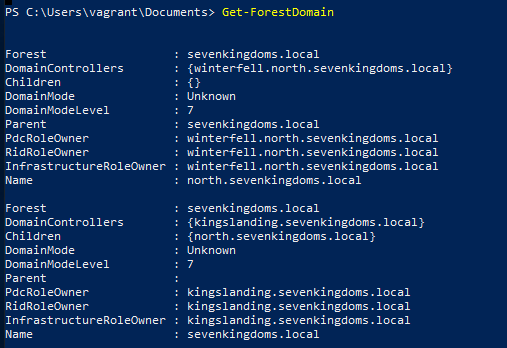
Get All Domains in the Current Forest
Command
Get-ForestDomainExample
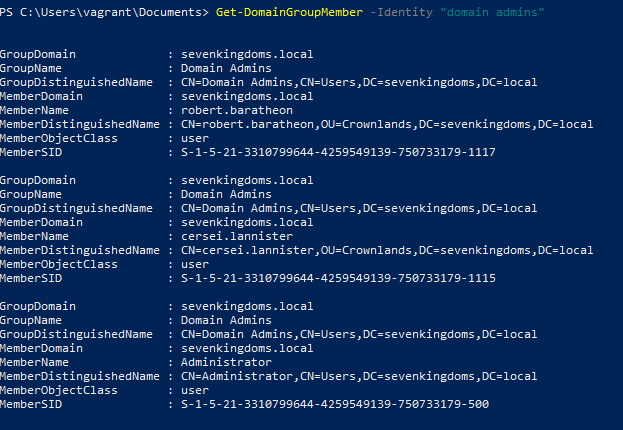
Get a List of Domain Members That Belong to a Particular Domain Group
Command
Get-DomainGroupMember -Identity "domain admins" -RecurseExample
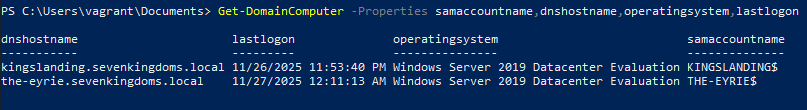
Get Domain Controller Computer Information
Command
Get-DomainComputer -Properties samaccountname,dnshostname,operatingsystem,lastlogonExample
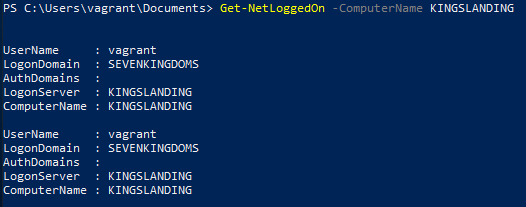
Get Logged on Users for a Computer
Command
Get-NetLoggedOn -ComputerName KINGSLANDINGExample
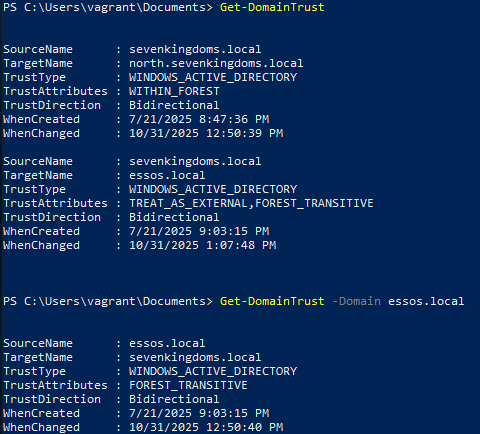
Get Domain Trust Information
Command
Get-DomainTrust # perspective of current domain Get-DomainTrust -Domain essos.local # perspective of a different domainExample
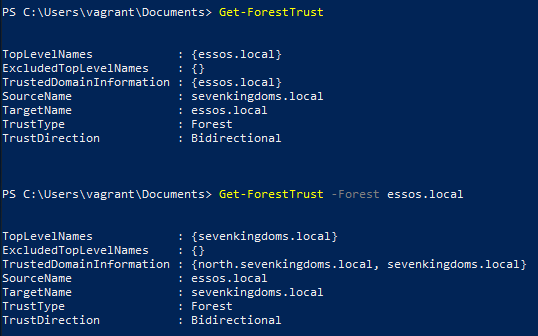
Get Forest Trust Information
Command
Get-ForestTrust # perspective of current forest Get-ForestTrust -Forest essos.local # perspective of a different forestExample
Enumerate Object ACLs
Command
Get-DomainObjectAcl -Identity "Domain Admins" -ResolveGUIDs -VerboseExample
INSERT_IMAGE_HERE
Get a List of GPOs
Command
Get-DomainGPO Get-DomainGPO -ComputerIdentity dcorp-student1Example
INSERT_IMAGE_HERE
Find all machines on the current domain where the current user has local admin access
Command
Find-LocalAdminAccessExample
INSERT_IMAGE_HERE
Find all machines on the current domain where the current user has local admin access using WMI
Command
Find-WMLocalAdminAccess.ps1Example
INSERT_IMAGE_HERE
Find all machines on the current domain where the current user has local admin access using PSRemoting
Command
FindPSRemotingLocalAdminAccess.ps1Example
INSERT_IMAGE_HERE
Find computers where a specific group has sessions
Command
Find-DomainUserLocation -UserGroupIdentity "RDPUsers"Example
INSERT_IMAGE_HERE
Get services with unquoted pathsand spaces in their name
Command
Get-ServiceUnquoted -VerboseExample
INSERT_IMAGE_HERE
Get services where the current user can write to its binary path or change arguments to the binary
Command
Get-ModifiableServiceFile -VerboseExample
INSERT_IMAGE_HERE
Get the services whose configuration current user can modify.
Command
Get-ModifiableService -VerboseExample
INSERT_IMAGE_HERE